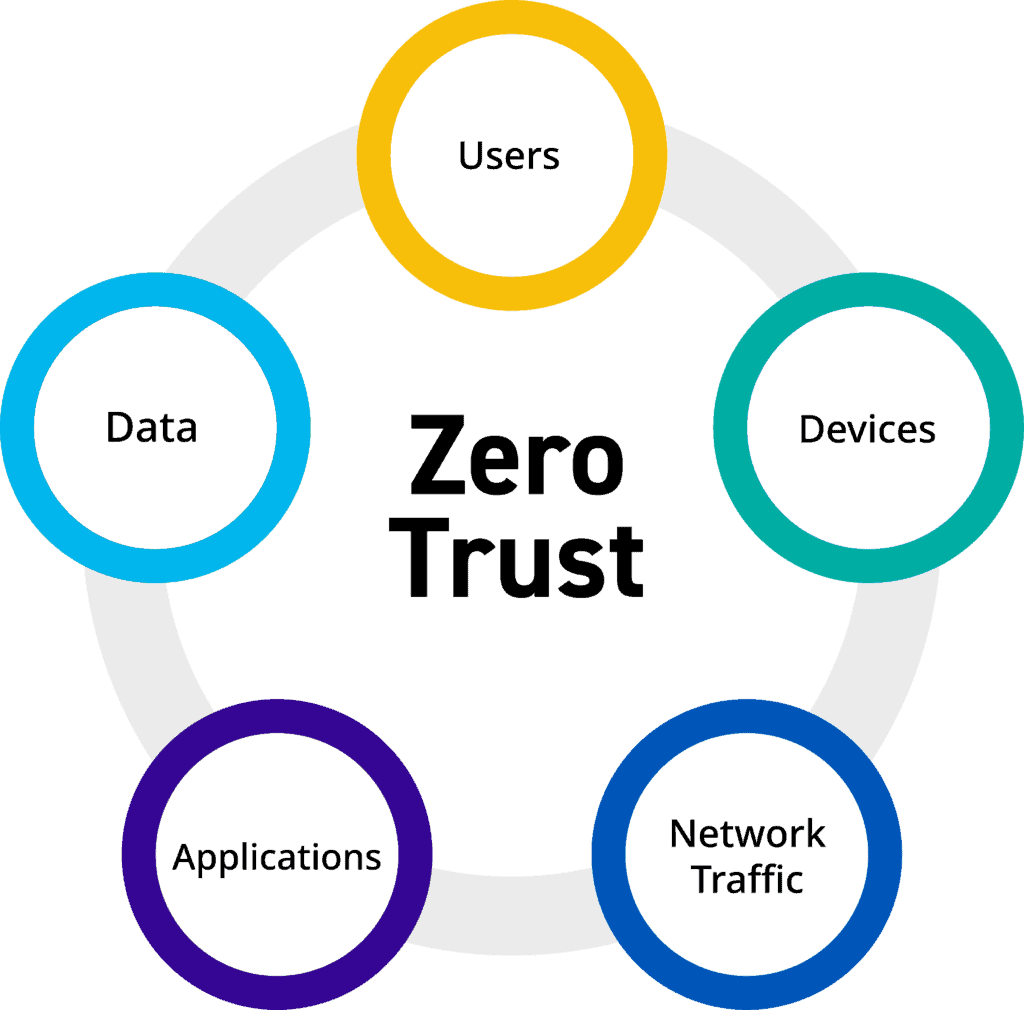
Zero Trust or Zero Trust Architecture is a security approach based on not directly trusting anything inside or outside the organization. The motto of this approach “never trust, always verify” well "never trust, always verify”. The Zero Trust approach does not depend on an application, user, etc. trying to connect to a system. It is an approach that advocates that verification should be done before granting access permission.
How Does Zero Trust Work?
Zero Trust is based on various technologies and management processes to ensure the protection of institutions' IT assets. For these processes in Zero Trust, first “protect surface” well “protective surface” It is carried out with the definitions called . The protection surface consists of data, assets, applications and services defined as critical. The protection surface may vary for each institution within the scope of the Zero Trust approach.
Once the protection surface is defined, it performs detailed control based on the users who want to access certain assets within the organization and their location, as well as other data. Zero Trust includes technology infrastructures such as multi-factor authentication, IAM (Identity Management), orchestration, encryption, scoring and authorization to perform these transactions. At the same time, it optimizes users' access rights and configures them to the necessary extent. Its infrastructure and technological equipment make Zero Trust extremely effective.
Zero Trust and Coverage
Zero Trust is not an approach that provides security specific to a single location. It is a security approach model that is actively present in the user's personal devices, systems, applications, in short, in every location and in every working device.
Considering that users working in the institution today access critical applications and data from locations outside the office, the importance of security controls connected to user devices or cloud-based is increasing. At this point, Zero Trust prevents data loss by providing secure user access-control regardless of location and where the data is (Cloud, SaaS, etc.). As sensitive data increases in cloud-based environments, corporate employees work independently from a single location. Zero Trust The importance of the security approach is increasing.