Evil Twin and EAP Downgrade attacks in WPA2-EAP networks,
In this article, we will examine evil twin attacks in corporate networks and Eap Downgrade attack vectors that allow us to obtain cleartext user information.
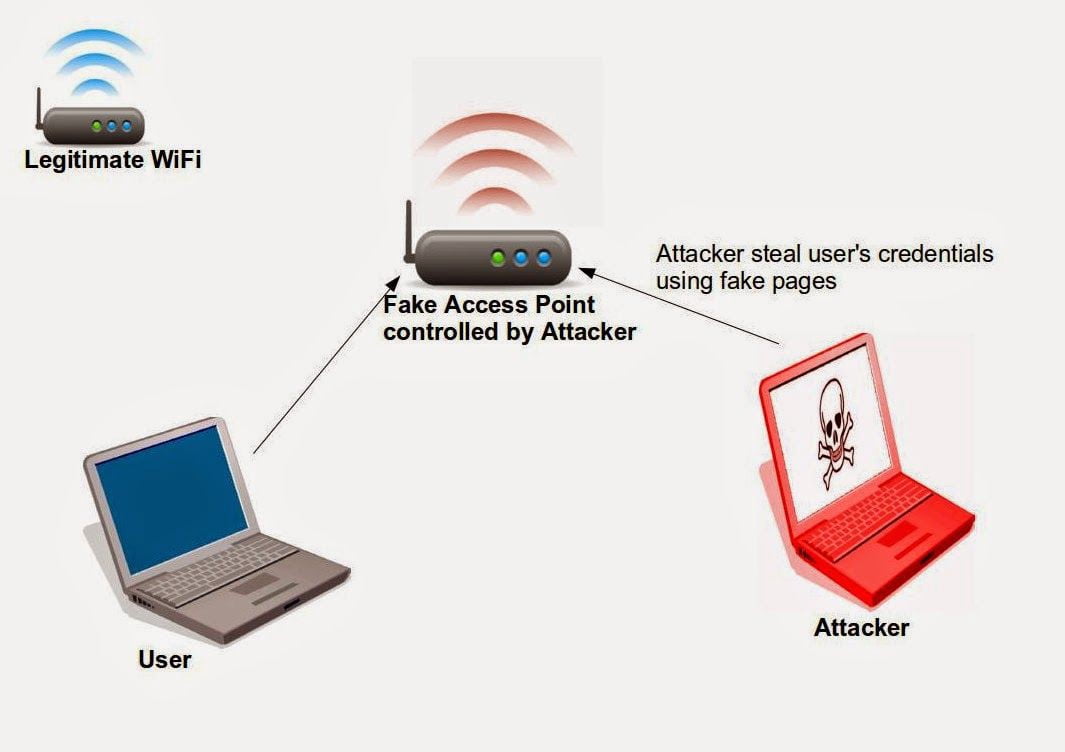
Evil Twin Attack
Evil Twin attack is basically a type of attack where an attacker imitates a wifi network used by users, makes a deauth attack on the users' network, knocks the users off the network, and allows the users to connect to the network of the same name created by the attacker without them realizing it.
WPA2-EAP
The most frequently used EAP applications are EAP-PEAP. EAP-PEAP authentication takes place between 3 technologies.
· Wireless Client
· Access Point
· Authentication Server (RADIUS)
Authentication takes place between the user, wireless client and RADIUS. When a user tries to connect to the network, the Authentication server presents the user with a certificate. If the client accepts the certificate, a secure connection is established between the Authentication Server and the client. Afterwards, the authentication process starts and if the authentication process is successful, the client can successfully access the network.
EAP Downgrade Attack
Before moving on to downgrade attacks, we need to know how the hostapd EAP user file and eap Negotiation (eap agreement) work. The Hostapd EAP user file works like a database. When a user tries to authenticate using EAP, hostapd searches the eap user file for the user by identity. When a matching line is found in the file, hostapd lists the EAP methods for the user from left to right, from most secure to least secure. It notifies the user about the method, and if the method is accepted, the user can access the network after entering his information. If the user does not accept the method, they move on to the next method. If there is no other method left, the user cannot log in to the network. As mentioned above, the methods are listed by default from the most secure method to the most insecure method. In order to be able to perform this attack, when we write it in the hostapd eap user file in a reverse way, the most insecure method is recommended at the first login of the user. If the user accepts this method, it causes the user to connect to the network using the cleartext method. In this way, the user's information is captured as cleartext.
We have come to the end of the theoretical part of our article. Now that we understand the theory of the attack, we can move on to the implementation part.
EAP Downgrade Attack
The name of the tool we will use to attack is eaphammer, you can access it from the link below.
https://github.com/s0lst1c3/eaphammer
First of all, to create a certificate;
./eaphammer –cert-wizard

After creating the certificate, we start the attack with the command used below.
./eaphammer -i wlan0 –channel 4 –auth wpa-eap –essid WifiAdi –creds

In the screenshot below, it asks the user whether they accept the certificate or not, as we stated in our article. We can show this as the breaking point of the attack. If the user does not accept the certificate, a slightly more secure eAP method is recommended. It tries to get permission from the user until the user accepts one of the methods or until the hostapd list runs out of methods. If the user does not accept any method, the authentication process fails.

If the User accepts the Certificate and completes the authentication processes, the password can be displayed in cleartext as you see below.

In this article, we explained evil twin attacks in WPA-EAP networks and the EAP Downgrade attack, which allows us to see user passwords in cleartext. As a security measure, people should be informed that they should not complete the authentication process unless they are sure that the certificate presented to them is secure.
https://solstice.sh/workshops-advanced-wireless-attacks/
https://www.youtube.com/watch?v=-uqTqJwTFyU
https://github.com/koutto/pi-pwnbox-rogueap/wiki/07.-WPA-WPA2-Enterprise-(MGT)