The Scary Dream of E-commerce Sites: Credential Stuffing
A technique that uses the risk posed by using the same email and password binaries on different platforms. Credential Stuffing, affects e-commerce sites the most…
What is Credential Stuffing?
"To our language"Identity StackingCredential Stuffing, which can be translated as ", appears as one of the feared techniques, especially in parallel with the astronomical development of e-commerce in recent years. What about Identity Stacking or as it is originally known? What is Credential Stuffing?
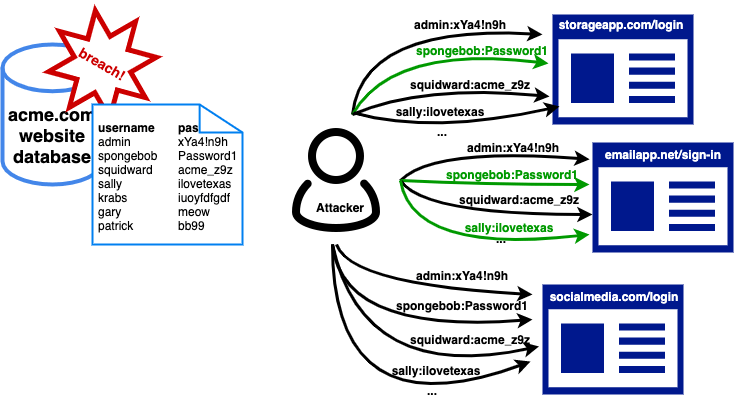
Credential Stuffing is a method obtained through trial and error brute force attacks, data leaks, or social engineering attacks. email:password, username:password or phone number:password It is an attack technique that allows users to take over users' accounts by testing duplicates on different platforms. OpenBullet, one of the tools used during Credential Stuffing, Usage and Features of OpenBullet It is explained in our article.
Bu teknikte sızdırılan kimlik bilgileri firma kaynaklı olmasa bile kullanıcıların %80’den fazlasının birden fazla platformda aynı parolayı kullanmasından dolayı ilgili firma için sorun teşkil etmektedir.
What is the Effect of Credential Stuffing on Companies?
As a result of Credential Stuffing, companies are affected by data leakage even if it is not caused by them. Companies whose customers' data are exposed cyber threat intelligence service They collect the leaked accounts and take the necessary actions by informing their customers of the situation.
Due to Credential Stuffing and sophisticated attacks, especially e-commerce sites are constantly cyber security consulting should take. Cyber threats frequently target the e-commerce sector, where credit cards are used extensively.
Companies that provide information security consultancy detect such attacks in advance, inform institutions and ensure that necessary actions can be taken faster. Threat intelligence and security to prevent an attack before it happens penetration test (penetration) It is a security measure that should not be overlooked.
What Precautions Can Companies Take Against Credential Stuffing?
Actions against Credential StuffingProfessional cyber threat intelligence service comes first. In addition, institutions can take precautions against Credential Stuffing by integrating the dual-factor authentication system into their own platforms, taking into account the user experience.
Enabling double-factor authentication provides a high level of security since the attacker will not be able to access the verification code that will be sent to the phone number or e-mail address specified by the customer in case the e-mail and password information of the customer are stolen.
Infinitum IT is struggling with Credential Stuffing. ThreatMonIT, the Cyber Threat Intelligence product developed by Infinitum IT, offers its partners the security service they need in an automated manner under the supervision of security analysts.