SSI Injection Vulnerability and Solution Suggestions
Before moving on to what SSI Injection vulnerability is, it is necessary to know the definition of the term Server Side Include (SSI).
What is SSI?
As it is known, websites are formed by the combination of more than one page and the pages can be changed dynamically through menus or from other areas. However, doing this manually is both tedious and time-consuming. Here is the solution to this handicap. SSI (Server Side Include) in Turkish "Server Side Addition“He comes to our aid. SSI allows us to add the required content dynamically on all pages.
SSI is a feature that allows developers to create web content dynamically with some special directives like “#”. Presenter html it searches and executes these special directives in order on its pages. These directives can be shell commands or files. After all directives are executed, the html content is displayed to the requester.
Example SSI directives:
<!–#echo var=”DOCUMENT_URI” –>
<!–#echo var=”DATE_LOCAL”–>
<!–#echo var=”REMOTE_ADDR” –>
What is SSI Injection Vulnerability?

SSI Injection The vulnerability is that web applications with SSI directives are exploited by the attacker. Such applications often accept data input from the end user and process it on the server. Such functionality is manipulated by the attacker by sending malicious SSI directives to the page, and as a result, the attacker can add, modify, delete any file on the server; can run shell commands or access sensitive file contents.
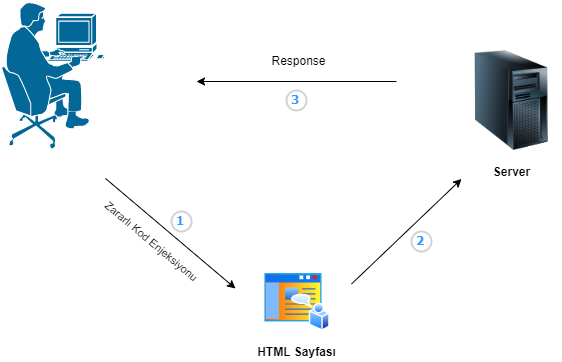
It is possible to examine the results of the vulnerability by sending SSI directives to a web application with SSI Injection vulnerability in the laboratory environment.

Image-1
As can be seen from Image-1, in the input field where the server can be interacted with in a web application. <!–#echo var=”DOCUMENT_URI”–> SSI directive has been given.

Image -2
Looking at the response from the server in Image-2, it can be seen that the full path (DOCUMENT_URI) of the resource from the URL has been obtained successfully.
In another example, it is possible to access sensitive data with the SSI vulnerability:

Visual-3

Image-4
How to Avoid SSI Injection?
Queries sent from web browsers to the server must be verified and queries containing SSI directives must be blocked. Again, using html encode methods, user queries should be checked before they are processed on the server, and harmful codes in the query should be pacified. The security level can also be increased by restricting the server to use SSI directives only where deemed necessary.