Open Redirect
This article is about how a URL redirection can harm a system, namely “Open Redirect” vulnerability will be examined in detail.
What is URL?
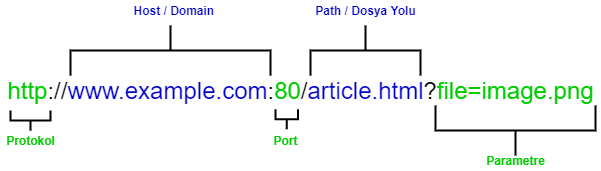
uuniform R.esource L.ocator (URL) means the unique address of any file or resource on the internet. This is an image file, HTML It can be a page or a style (CSS) document.
URLs are divided into a number of segments. Protocol, domain/host First Name, port And path -file path etc. These sections, designated as , guide the web browser with instructions on how to access the target resource.

Simple URL Structure
What is Open Redirection?
Many developers use some simple functions when coding their websites, sometimes to request data from external sources and sometimes to direct their users to different locations. in PHP header(), in Python redirect() like.
However, these redirects are often not filtered properly and allow users to enter the data they want. “Open Redirect” vulnerability occurs.
Although it may seem like a minor vulnerability on its own, it can turn into an effective security vulnerability when it can be used together with vulnerabilities such as "RCE" and "XSS".
Let's examine a simple example to explain the subject better.

In the above php code block header() using the function $_GET caught with superglobali url It can be seen that a simple orientation is made to the value of the parameter. The value of the url parameter sent from the Index.php page ( https://www.infinitum.com.tr ) It can be seen more clearly when the code block is run on localhost that the page is captured and redirected to this address:

If the http request that occurs when the relevant link is clicked in the image above is examined with a web proxy tool:

As can be seen in the request captured by proxy php Since no filtering is done in the code block, this step url The parameter can be directed to any desired address.

At this stage url= When the value of the parameter is changed to http://www[.]google[.]com and the request is sent to the server, it will be seen that the operation is successful:

Encoded Redirection
In some cases, developers may change the value of the parameter to be routed for greater security. URL-Encoding or Base-64 Encoding change with their methods. However, since these methods are a one-sided masking method, they can still be detected if the method used is known. url redirect They can be used to exploit vulnerabilities. Now let's examine these two different issues separately.
Url Encoded Redirection
Url Encoding, some harmful characters (such as < >) url It is one of the most used encoding methods by developers to prevent encoding. The issue will become a little clearer when the PHP code below is examined.

As you may remember from the first part, the code snippet here is a redirect code written in PHP. Unlike the first example, this code is pre-encoded url data from the parameter urldecode() function and directs it to the relevant address. Redirection operations can be seen more clearly by running these codes on localhost:

On the web page shown above http When the request is examined with a web proxy, the masked url can be seen with the url encode method:

In the visual url which is the value of the parameter https://www.infinitumit.com.tr/ It can be seen that ' is simply url encoded. At this stage, the address to be directed to must be masked with url encode before entering it into the relevant field.

The relevant value can be obtained by encoding the URL with Burp Suite's Decoder tool or any other tool, as seen above.

Finally, the obtained value is entered into the relevant field (url=) is entered and when the http request is sent again to the server, it will be seen that the redirection has been successful.

Base64 Redirection
URL Encoding is not the only encoding method that developers implement in their projects. For a safer routing process base64 The encoding method is also used by developers. If we consider again the php code block used in the previous sections:

This time in the simple routing process index.phpMasked with base64_encode() function from url value of parameter, $_GET Caught with his supergloabal base64_decode() It is converted back to normal state with the function. When the relevant code is run on localhost, it can be seen that the url is masked with base64 in the bottom panel of the browser.

At this stage, when the http request is examined using a web proxy, the base64 value of the directed address can be seen again:

With the help of a base64 encoder, the base64 value of the address to be redirected (http://www[.]google[.]com) can be obtained:

The resulting base64 value is captured in the web proxy url When the parameter is changed to its value and the request is sent to the server, it will be seen that the operation is successful:


Open Redirect Vulnerability Precautions
- Data from users should be verified by filtering appropriately.
- Developers should work with lists of trusted URL addresses.
- The web application must notify with a warning when the user tries to redirect to an untrusted URL.
- Developers should prioritize connecting with custom links rather than using a redirect function.