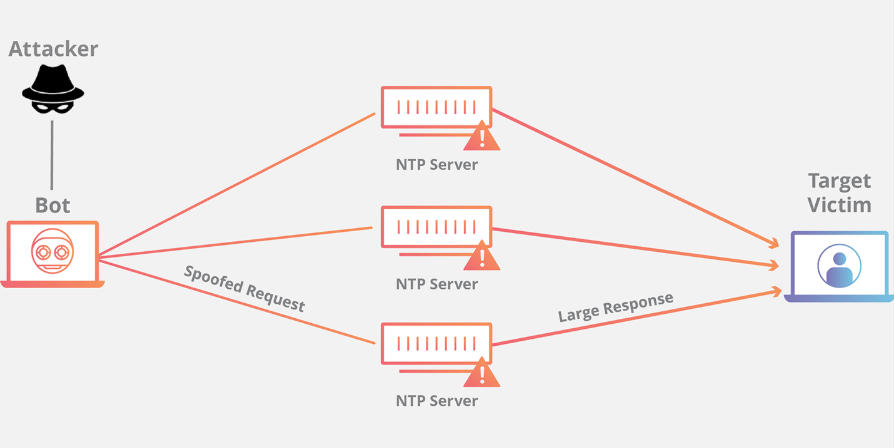
What is NTP Amplification?
NTP Amplification attack; An attacker can use a Network Time Protocol (Network Time Protocol) to overwhelm the targeted network or server with large amounts of UDP traffic.NTP) function that uses DDoS is the attack. It makes the target and surrounding infrastructure inaccessible to regular traffic.
How to Perform an NTP Amplification Attack?
NTP Amplification Attacks mostly take advantage of the bandwidth inequality between the opposing system and the attacker. It is possible to define bandwidth inequality as the attacker sending the requests creating traffic higher than the target's bandwidth upper limit. In this way, we send more requests than the system can respond to, and the network bandwidth may be exceeded and the network structure may be disrupted. The traffic sent can be further increased by using botnets.
NTP Amplification Scenario
DDoS attacks are carried out to disable target systems. NTP Amplification DDoS is one of the most effective methods of attack. In order to realize this management;
- There is a DDoS tool called NTPDoser for requests to be sent to NTP servers.
- NTPDoser is made executable by compiling the NTPDoser file with the command “gcc NTPDoser.cpp -o NTPDoser -lstc+ -pthread”
- Necessary settings for the NTP Amplification attack can be made by running the “./NTPDoser [Target IP] [Number of Threads] [Attack Time]” command.
- The attacker needs botnets to hide himself and increase the intensity of the attack.

Precautions That Can Be Taken Against NTP Amplification Attacks
Like many other DDoS threats, NTP Amplication attacks are difficult to block completely because responses from NTP servers appear as legitimate traffic on valid servers. However, there are some precautions that can be taken:
- Thanks to its enormous volume, DDoS traffic can easily bring down even the most resilient network structures. By using appropriate filters, users who generate traffic above the specified amount can be excluded from the system.
- Protection against volumetric DDoS threats can be achieved by leveraging an optionally metered global scrubbing network to deflect multiple 10Gbps DDoS threats, including NTP Amplification attacks.
- By verifying the source IP, fraudulent packets arriving on the network can be prevented. If a packet is routed from inside the network to a source IP address that appears to be outside the network, the packet is understood to be fraudulent and blocked.
- On NTP servers monlist Amplification attacks can be prevented by disabling the command and applying ingress filtering to networks that allow spoofed IPs.
- The number of NTP servers that support the monlist command can be reduced or disabled. To avoid being affected by the Monlist vulnerability, NTP software prior to version 4.2.7 should not be used. Software prior to version 4.2.7 must be updated.
NTP Amplification In order to take precautions against attacks such as these, DDoS tests should be performed regularly. To learn about the professional DDoS service, you can visit the Access Denial Testing page.
