Cross-Site Scripting (XSS) It occurs with the interpretation of the HTML engine on the browser side by directly pressing the input received from the user on a website to the screen again. Since there is no filter and encoding, the attacker can run JavaScript and HTML codes in this area to infiltrate the target.
What are XSS Attack Types?
There are 3 types of XSS attacks:
- Reflected XSS: It comes directly from the HTTP request.
- Stored XSS: Income from the database, also referred to as permanent.
- DOM-based XSS: It is a type of XSS that is born within HTML objects as a result of insufficient control of the objects.
What is Reflected Cross-Site Scripting?
Occurs when an application receives data in an HTTP request and insecurely incorporates that data into the immediate response.
http://domain/path/endpoint.php?variable=DATA
In the form of a connection example; It receives a "variable" data that exists in endpoint.php, if this data (DATA) is directly included in the content, it will be here. Reflected XSS weakness will occur.
<script>alert(document.cookie)</script>
After a JS code sent in the form returns from the remote server, it is interpreted by the browser's HTML engine and our cookie value is printed on the screen.
What is Stored XSS?
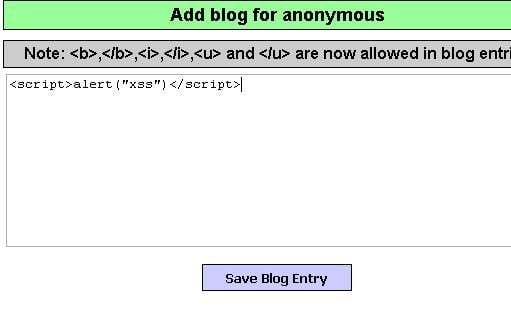
This type of XSS, which seriously threatens web application security, is a persistent type of XSS, the parameters received in the input are written to the database. aka “Persistence XSS” is defined as. Since it is written to the database, every user who calls from the database repeatedly and continuously after manipulation with any JavaScript and html code is affected.

As in the example above, malicious codes written when there is no control on the inputs processed into the database will be called from the database as it is, and will be interpreted and run by the browser engine.
After the JS code written in the picture above is interpreted, an alarm in the form of "xss" is received on the screen.
What is DOM-based XSS?
Document Object Model, “DOM” also stands for “Document Object Model”. It is an XSS vulnerability that arises in the objects that we access with JavaScript in the HTML document. It takes its inputs after the generic “#” sign. Therefore, they are not sent to the server and the processed data remains on the browser side. After processing the input with JavaScript, the object acts accordingly. At this point, DOM XSS is born as a result of insecurely designed or insufficient encoding operations.
Solution Suggestions Against XSS Vulnerability
All input from the user should be considered insecure. In this manner;
- The accuracy of the input,
- Sterilize the Input,
- The input must have gone through the encoding process.
Every encoding process should be done in accordance with the content.
that cause critical or high levels of findings in penetration testing studies XSS vulnerability It is a vulnerability that requires quick action and significantly reduces system security.