What is Cyber Security? Cyber Security Recommendations for Companies
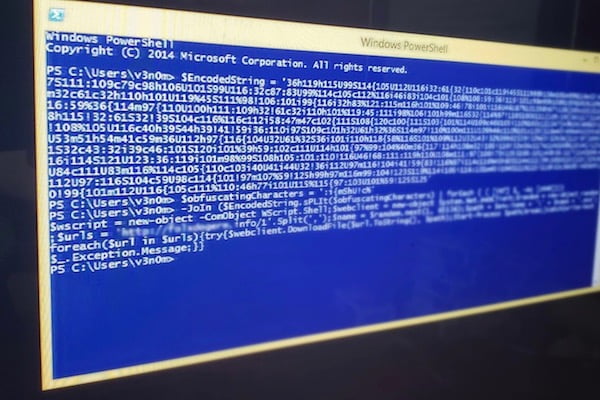
Cybersecurity refers to the practices and technologies used to protect internet-connected systems, including hardware, software, and data, from attack, damage, or unauthorized access. Why is Cyber Security important? Cyber security becomes more and more important as institutions, organizations and individuals increase their dependence on technology.